Awake/Arista 2022 Network PCAP CTF Challenge
After filling out the Google Form to register and receiving the PCAP, I opened it in Wireshark and searched for “instructions”.
I found the string in TCP stream starting from packet 686. I exported the page WELCOME.html with File→Export for a better reading experience.
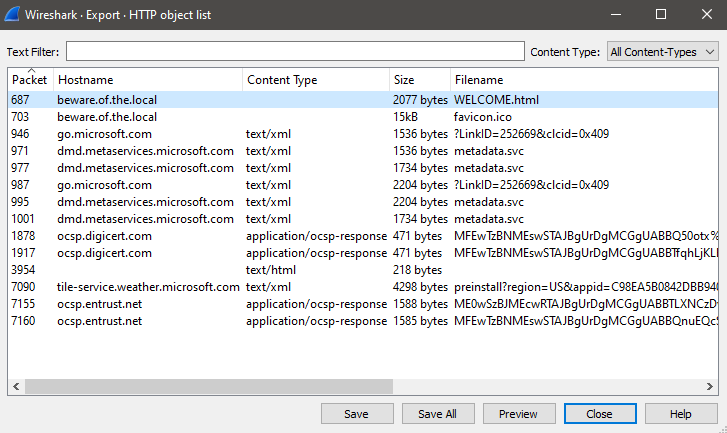
The important notes from that file are:
- Find the final key and send it to Gary and Ryan.
- There are a ton of weird little references, jokes, etc through the puzzle. When sending us the final key, also tell us about the ones you noticed and you might get even better prizes.
- Don’t post solutions until after August 11, 2022.
- Help is at: 2022pcap-help@arista.com
Found a cia.gov request with a response from Server: AkamaiGHost. Redirecting from cia.gov to www.cia.gov is normal behavior that occurs if you try it yourself.
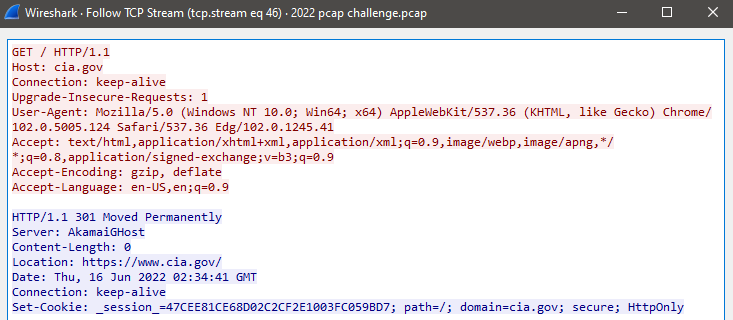
Here’s an old thread about AkamaiGHost: https://seclists.org/pen-test/2003/Oct/7
Checking in tcp.stream eq 109, packet 9870 contains a session setup request for a user \Ignatius.Donnelly. His research below appears in line with his character.
Ignatius Loyola Donnelly was an American Congressman, populist writer, and fringe scientist. He is known primarily now for his fringe theories concerning Atlantis, Catastrophism, and Shakespearean authorship, which many modern historians consider to be pseudoscience and pseudohistory. -Wikipedia
In this stream, he requests several files:
- \Desktop-9o38l3m\confidential
- SR66_Russia-ChinaRelations.pdf
- 07_CHINAS-NATIONAL-SECURITY-STRATEGY.pdf
- ATA-2021-Classified-Report.pdf
- cousins.jpg
- dndbbs.txt
- The Dungeons and Dragons Bulletin Board Service text adventure system
- family photo.jfif
- family2.jpg
- Hypersonic Weapons.docx
- Power competition with China and Russia.pdf
- security strategies of china russia eu.pdf
The file dndbbs.txt contains a base64 encoded string. Let’s chuck that into the decoder.
$ echo WlVjNWVVbEhkR3hsVkc5blRVaG9hRmxSUFQwPQ== | base64 -d | base64 -d | base64 -d
xor key: 0xaa
If you XOR 0x00 with 0xaa, you get 0xaa. I found many A’s in tcp.stream eq 125. I showed data as raw, Saved as…, XORed it using https://github.com/mstrand/xcat, and checked the filetype of the result.
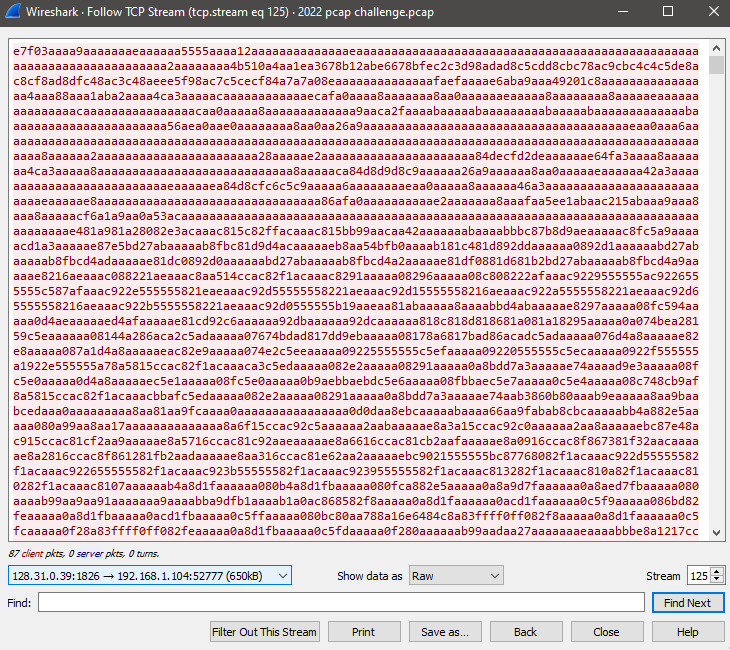
$ cat data | python3 xcat.py -x aa > out
$ file out
out: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
Let’s run the executable (in a sandbox). If you have no internet you get the following:
If you do have internet, you get this screen and the creation of gate2 in the same directory:
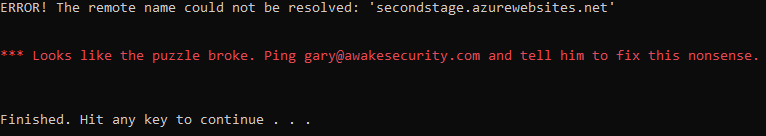
Running gate2.exe, you get an empty terminal screen that doesn’t print anything or close upon input. However, this is a networking-based CTF so let’s sniff some packets. The error running gate1 without internet made me think to search for azurewebsites.net:
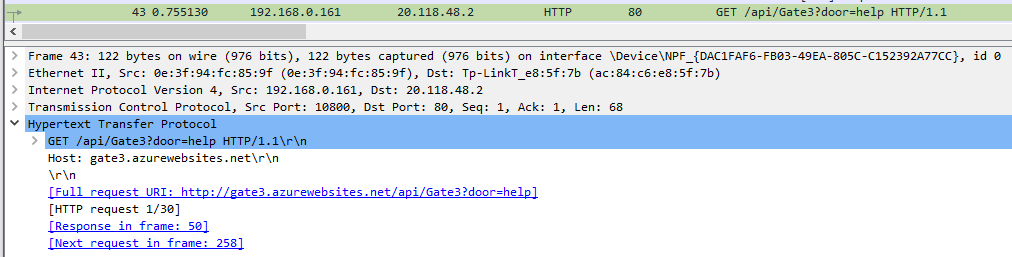
What is at this link? Just before I set up a brute-forcer, I found the solution.
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=help
To see what's behind a door, pass the door number you'd like to look behind. Eg: ?door=1
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=key
You cheeky little thing, you! Look at you testing me. I love it! But, don't waste your time.Pass ?door=help for a reminder about how this works.
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=0
Haven't you ever seen an old gameshow? Door 1, 2, or 3. It always works that way...
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=1
Good as place as any to start, right? Try door #3.
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=3
Very good at following directions. Door #2 is better though.
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=2
Sorry, I meant go to door 5. Really.
noble@heart:~$ curl http://gate3.azurewebsites.net/api/Gate3?door=5
YOU DID IT! Parties and/or prizes await! Pride and glory available for immediate use!
As proof of your conquest, and to receive further prize and party details, email 2022pcapchallenge@arista.com and include the following key:
0xd68f76878c4832<censored>421a810d8697bd62